
Check Point DDoS Protector X200
Next-Generation DDoS Protection and Attack Mitigation Appliance

Sorry, this product is no longer available, please contact us for a replacement.
Overview:
Adaptive Protection from the Most Advanced DDoS Threats
Distributed denial-of-service (DDoS) attacks are increasing in frequency and ferocity. Powerful IoT-botnets for hire over the dark web make launching large-scale attacks accessible, effortless, and cheap. Professional hackers are continuously seeking new ways to disrupt the flow of network traffic and undermine the user experience, resulting in loss of revenue, tarnishing of the brand and increased customer churn rates.
DDoS Protector, Check Point’s real-time perimeter attack mitigation device, secures organizations against emerging network multi-vector attacks, powerful DDoS campaigns, IoT botnets, application vulnerability exploitation, malware, and other types of cyberattacks.
Automated Zero-Day Attack Defense
Behavioral-based detection and mitigation to defend against unknown zero-day attacks without impacting legitimate user experience
Keyless SSL/TLS Flood Mitigation
High-capacity keyless protection from SSL/TLS-based DDoS attacks without adding latency to customer communications and while preserving user privacy
Advanced Attack Protection
Detection and mitigation of today’s most advanced attacks, including Burst attacks, Domain Name System (DNS) amplification attacks, IoT botnet floods, Layer 3–7 and other crippling DDoS attacks
Patent Protected Real-Time Attack Signature
Automated signature creation and advanced challenge escalations to achieve the highest mitigation accuracy that can automatically mitigate unknown attacks and minimize the impact on legitimate traffic
Scalable Management & Complete Visibility
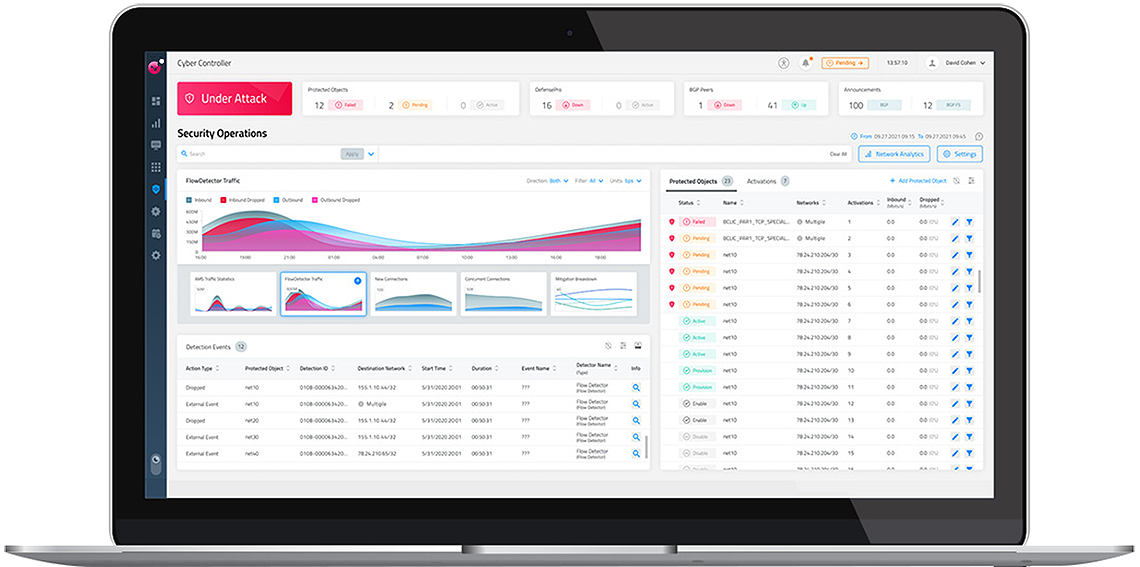
Simple Management Dashboard
The new dashboard allows admins to easily navigate and quickly view detection events, apply policies, or refine configurations, all from the same window.
Network Analytics
Network Analytics with comprehensive visibility of traffic stats at any time.
Complete Visibility
Unified visibility and control for both out-of-path and inline DDoS protection solutions, optimized troubleshooting, and enriched search and filter capabilities.
Multiple Deployment Options
Multiple deployment options offering broad protection and mitigation capacity (6Gbps to 800Gbps), virtual appliances and integrated hybrid solution.
Pricing Notes:
- Pricing and product availability subject to change without notice.

