
Collaborative Security - Infinity ThreatCloud AI
With Check Point defending your business, you are empowered with enhanced and precise prevention capabilities against the most sophisticated attacks. This is made possible by the formidable intelligence of Infinity ThreatCloud AI, the central nervous system for our security solutions.

Prevention first
Fastest block attack rate to prevent attacks

Best catch rate
With both known and unknown threats

Near zero false positives
Regain time that would be lost addressing false alarms
How ThreatCloud AI Works
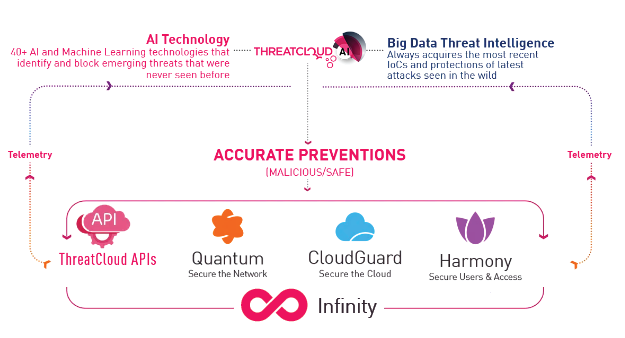
As part of Infinity Core Services, ThreatCloud AI aggregates and analyzes big data telemetry and millions of Indicators of compromise (IoCs) every day. Our threat intelligence database is fed from 150,000 connected networks and millions of endpoint devices, as well as Check Point Research (CP) and dozens of external feeds. Over 50 engines are packed with AI-based features and capabilities.
ThreatCloud AI employs advanced AI with over 50 technologies to detect and neutralize novel threats, using big data to update its defenses with the latest Indicators of Compromise. It analyzes telemetry data for precise threat categorization, enhancing security across networks with Quantum, cloud with CloudGuard, operations with Infinity, and user access with Harmony.
Check Point Protects Your Everything with Accurate Prevention
Over 50+ Engines Packed with AI-based Features and
![]()
Unknown Malware Detection
Infected hosts detection, sandbox static analysis for executables, documents, and macros
![]()
Zero-Day Phishing
Network and mobile zero-phishing detection, anti-phishing AI engine, email static analysis, and HTML body NLP
![]()
Classify
Documents meta classifier vectorization family classifier, XDR/XPR incidents aggregation, ML Similarity Model, MRAT classifier, IP Port
![]()
Improve Accuracy
Network AI and mobile AI engines aggregator, machine validated signature
![]()
Anomaly Detection
Cloud networks anomaly detection, XDR/XPR user behavior analysis, SSH tunneling
![]()
DNS Security
DNS tunneling, DGA domain generation algorithm
![]()
Campaign Hunting
ThreatCloud AI Campaign Hunting
![]()
Expose Stealth Breaches
Analyst Mind, Malicious Activity Detection
Featured Threat Prevention Engines
| Engine Name | Security value | Method | Technology |
|---|---|---|---|
| DeepTunnel | DNS Tunneling | AI | Deep Learning |
| Ditto – Detect Malware & phishing (DeepPDF) | Detect Malware according to PDF layout | AI | Machine Learning |
| Brand spoofing detection | Detect Phishing websites using image similarity | AI | Machine Learning |
| Mobile Zero-Phishing detection engine | Mobile Zero-Phishing detection engine | AI | Machine Learning |
| Zero-Phishing | Detection of zero-day Phishing websites based on page content | AI | Machine Learning |
| Memdive | Dynamically extract the hidden malicious payloads out of process memory | AI | |
| ThreatCloud graph | Deciphers complex attack patterns | AI | |
| TEX – Exploitable content Disarm and reconstruction | Remove Active Content from Documents | Traditional | Traditional |
| IPFS | Scans the URL and detects suspicious IPFS patterns | Traditional | Traditional |
Use Cases for ThreatCloud AI

Threat Extraction – Check Point’s Content Disarm and Reconstruction (CDR)
Threat extraction is a Content Disarm and Reconstruction capability of Quantum network and Harmony Endpoint, powered by ThreatCloud AI, the brain behind all of Check Point’s products, Threat extraction: real-time threat prevention that never disrupts the flow of business and provides best security.

Proactively prevent emerging threats
- Browsing web pages
- Filling out electronic forms
- Typing-in credentials
- Receiving emails
- Download documents

