Benefits:
Discover bot outbreaks, detect APT attacks and stop bot damage
- Detect infected hosts with unique Multi-tier ThreatSpect™ engine
- Combine information on remote operator hideouts, botnet communication patterns and attack behavior to accurately identify bot outbreaks
- Receive up-to-the-minute bot intelligence from the ThreatCloud knowledgebase
- Prevent damage by blocking bot communication between infected hosts and a remote operator
Real-time security intelligence delivered from ThreatCloud
- Leverage industry's first collaborative network to fight cybercrime
- Analyze over 250 Million addresses for bot discovery
- Dynamically update attack information from worldwide network of sensors and industry’s best malware feeds
First Integrated Anti-Bot Network Solution
- Integrate all critical threat prevention technologies in a single gateway – IPS, AV, Anti-SPAM, URL Filtering and Anti-Bot
- Set policy and view infection reports that are fully integrated with the Check Point Antivirus Software Blade
- Investigate infections and easily assess damages with extensive forensics tools
Features:
Complete Anti-Bot Solution
Complete Anti-Bot Solution - integrated into Check Point Software Blade architecture
- Discover, stop and assess bot damages on a single gateway
- Unified and centralized management
- Integrated with Check Point Antivirus Software Blade
- Available on every gateway
ThreatCloud™ Real-time Security Intelligence Feeds
ThreatCloud is a collaborative network and cloud-driven knowledge base that delivers real-time dynamic security intelligence to security gateways. That intelligence is used to identify emerging outbreaks and threat trends. ThreatCloud powers the Anti-Bot Software Blade allowing gateways to investigate always-changing IP, URL and DNS addresses where Command and Control Centers are known. Since processing is done in the cloud, millions of signatures and malware protection can be scanned in real time.
ThreatCloud’s knowledgebase is dynamically updated using feeds from a network of global threat sensors, attack information from worldwide gateways, Check Point research labs and the industry’s best malware feeds. Correlated security threat information is then shared among all gateways collectively.
Multi-Tier ThreatSpect™ Bot Detection Engine
Multi-Tier ThreatSpect™ Bot Detection Engine - the Anti-Bot Software Blade discovers infections by correlating multiple detection methods
- Reputation – evaluating IPs, URLs, and DNS addresses to determine whether outbound traffic is destined for known botnet Command and Control (C&C) sites.
- Patterns - detecting unique botnet family communication patterns (over multiple protocols such as HTTP, DNS and SMTP)
- Bot damages & actions by detecting attack types, such as Spam (leveraging outbound mail analysis) and Click fraud, as well as anomalies (irregular ports, protocols)
- Security intelligence is updated in real-time by ThreatCloud
Inline Bot Prevention
Inline bot prevention – block bot communications from infected hosts
- Support Inline and out-of-band deployment topologies
- Block bot specific communication to C&C sites to neutralize bot damages
- Ensure work continuity by blocking only bot traffic, yet allowing good traffic to continue
Integrated Malware Reports and Dashboards
Malware reports and dashboards are integrated with the Antivirus Software Blade with infection summaries and trends to provide better visibility to organizational malware threats and risks
- View infected hosts statistics, malware types and activities, trends/changes vs. previous week/month, amount of data sent or received and more
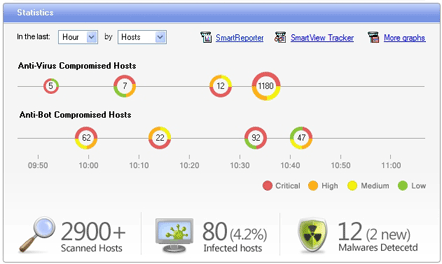
Summary of infected hosts
Extensive Forensics
Forensics - Provide administrators and security teams with the information they need to analyze security events, investigate infections and assess damages
- Detailed infection information per malware type and/or infected users and machines
- Identify bot names, amount of data sent and infection severity
- Key bot actions – identify suspicious activities such as participating in DDoS attacks, self-distribution attempts, and participating in click fraud
- Threat Wiki – extensive infection information (malware type, description and any available details such as executables run, used protocols etc.)
- Packet capture – view data sent using complete per-session packet capture with SSL inspection
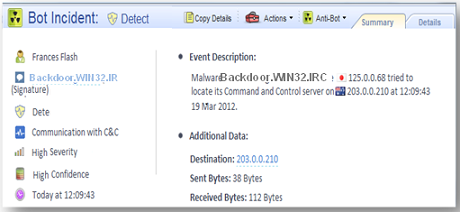
Extensive Forensics

![]()



