May 28, 2019 By BlueAlly

Recently, a security advisory was released for a vulnerability in RDP (Remote Desktop Protocol) affecting multiple Windows Operating Systems prior to 8.1. According to Microsoft’s advisory, this vulnerability can be exploited for both remote code execution and denial of service attacks. All this without needing the credentials of the target machine.
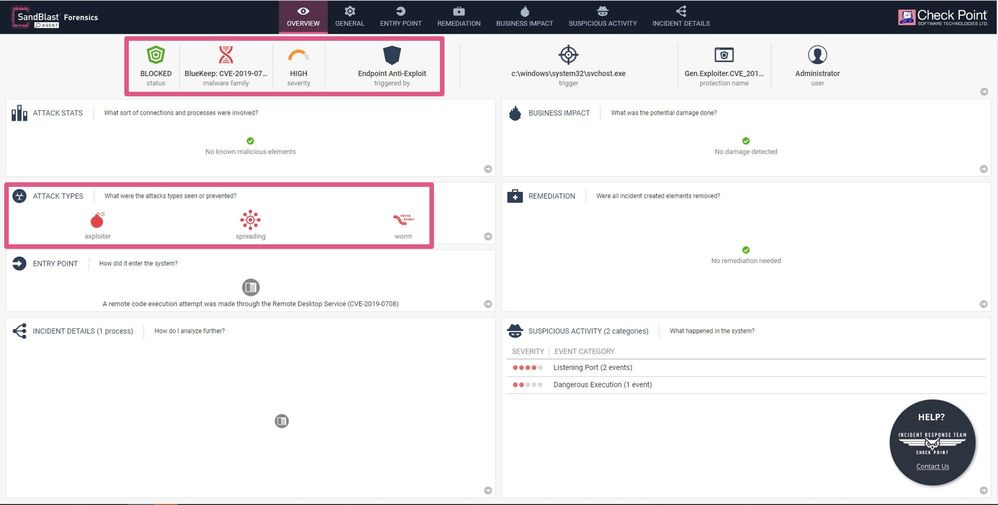
Check Point’s SandBlast Agent Anti-Exploit now monitors the RDP service for both Windows 7 and Windows 2008R2 and is able to prevent this attack from occurring. Not only is SandBlast Agent able to prevent the exploit from being delivered on unpatched systems, but it is also able to prevent the exploit from being delivered to the previously vulnerable driver in patched systems.
The protection is available in SandBlast Agent’s E80.97 Client Version (Can be downloaded from sk154432).
To see Anti-Exploit’s protection in action please see the following video, where our Threat Research Group’s POC used for exploitation is blocked. In addition, you can also see how we are able to block the scan of the Metasploit module that was recently developed to identify vulnerable systems.
SandBlast Agent BlueKeep Event Forensics Report: