July 10, 2020 By BlueAlly

An internal security analysis revealed a new attack method, which bypasses default security (EOP) and advanced security (ATP) layers. This was detected when analysts noticed a suspicious increase in .slk files sent to some Office 365 accounts a couple of weeks ago.
In the attack, cyber criminals send an email with an attachment in the form of a .slk file that contains a malicious macro (MSI executable script), allowing them to control infected machines remotely, by installing a Remote Access Trojan. This attack is extremely sophisticated, and meticulously designed to bypass security tools.
How does the attack bypass advanced protection?
The attack specifically targets some Office 365 accounts. The email body and the malicious attachment are constructed in such a way that easily tricks users to believe the email came from a customer or partner they know, and therefore increases the likelihood of them opening the SLK file.
A quick explanation about SLK files: these outdated files are a Microsoft human-readable, text-based spreadsheet format. They were used as an open-format alternative to proprietary XLS files, before XLSX was introduced in 2007. In this attack, the hackers use these files since they look like normal Excel sheets to the end user, while allowing the hackers to bypass Advanced Threat Protection (ATP).
The first version of this kind of SLK files attacks were seen in 2018 and were eventually blocked by Microsoft ATP. However, this new attack includes a few obfuscation methods specifically crafted to bypass Microsoft’s ATP:
- Hundreds of disposable Hotmail accounts were used to send the malicious emails, each sending a small number of emails at a time.
- The malicious macro script included ‘^’ characters to throw off Microsoft’s ATP filters, taking advantage of the filters not interpreting text the same way Microsoft command line does. By adding ‘^’ to the script it becomes unreadable to the ATP filters, but can still run as the original script by the desktop command line.
- In order to avoid ATP reading the URL as a web link, it was split in two. The first macro command created a batch file with the first half of the URL, and the second added the remainder URL and then runs the batch file.
- The hackers activated the hosting server only after the malicious email was sent, so the server would seem harmless in case ATP sandboxed it.
- The hosting server would ignore all queries besides “Windows Installer” user agents, which is a common method to ensure the server responds only to the malicious script, thus avoiding detection by URL analysis tools.
What can these malicious emails do?
If the attack is successful, the cyber criminals can control the infected machine and access all the information on it, whether it is sensitive data, confidential files, saved passwords and even saved payment methods, all potentially leading to critical business disruption and financial losses.
How does Check Point CloudGuard SaaS protect impacted Office 365 customers?
Check Point CloudGuard SaaS customers are protected from these kinds of attacks. CloudGuard SaaS blocks these attacks by leveraging its advanced sandboxing technology, Threat Emulation. As seen in the report below, there were several indicators ranging from file system events to network events that caused the attack to be flagged as malware, and therefore blocked.
Sign up for Check Point's live webinar to learn more about how CloudGuard SaaS blocks the most advanced attacks.
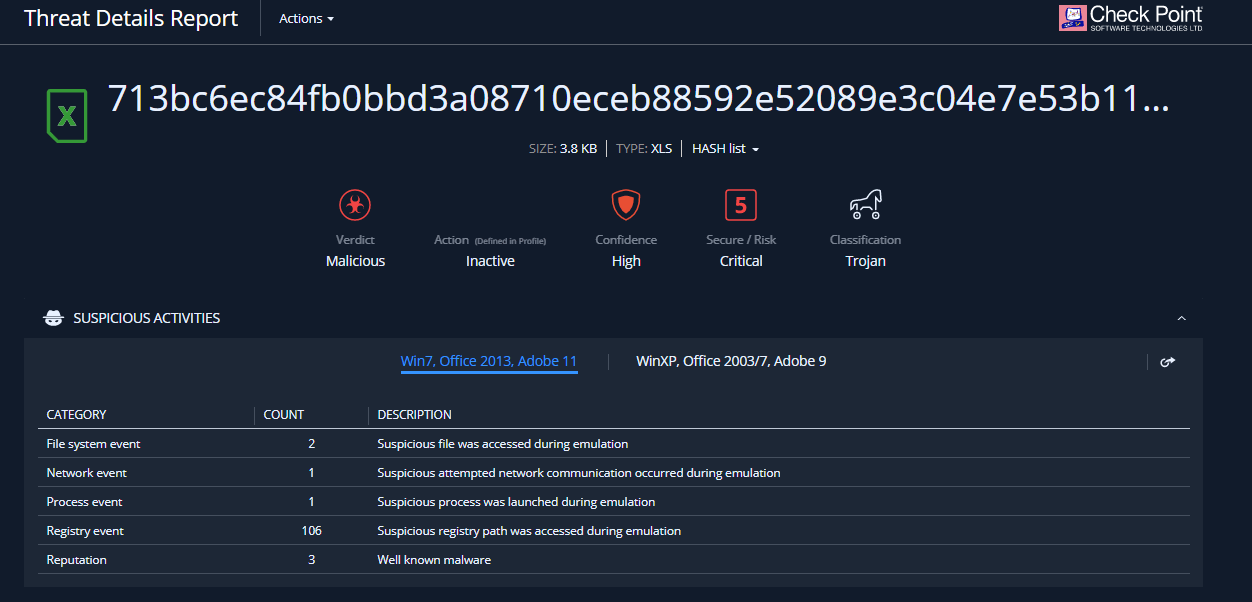
Furthermore, CloudGuard SaaS admins can gain additional insights by examining the emulation videos as well as the way the malware behaved over time. This type of advanced analytics allows administrators to not only become more educated about the attacks their organizations are facing, but also know that they have a security product that they can trust.
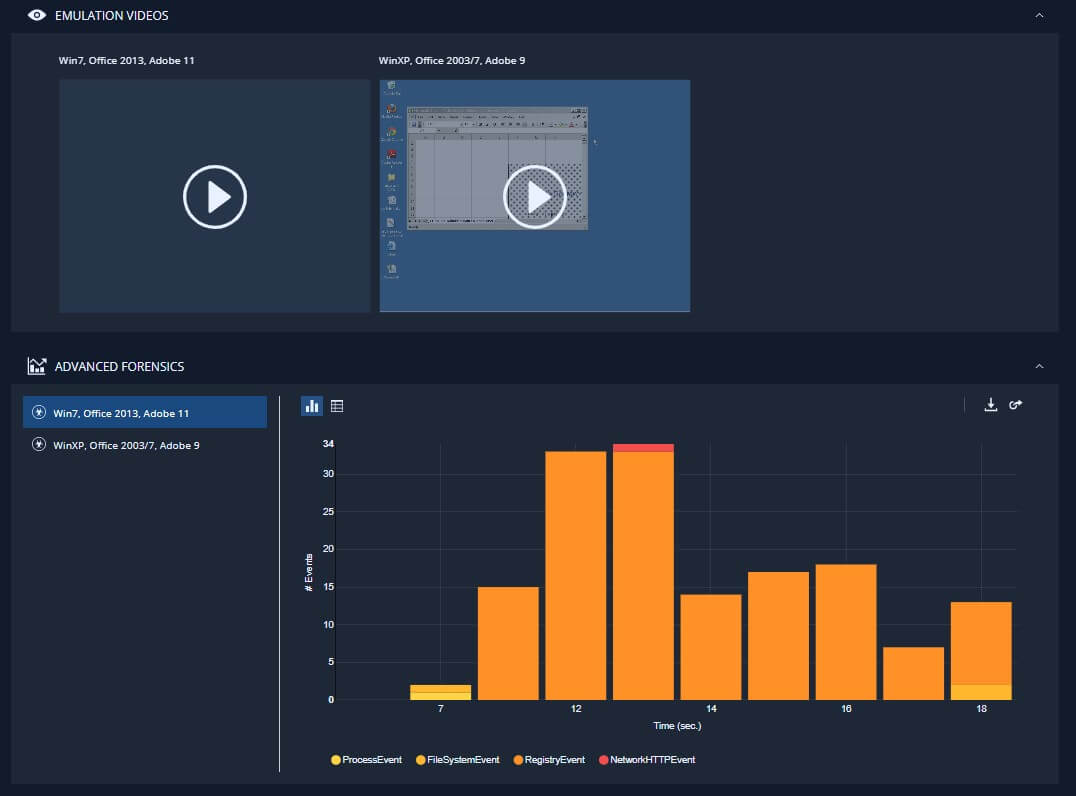
To get the best results, it is recommended to put CloudGuard SaaS in Prevent (Inline) mode. This way the attack will be stopped before it can ever reach the users’ mailboxes.
